Self-signed certificate chain problems with GitHub Copilot and Visual Studio and Visual Studio Code
My customers have been excited to start using and experimenting with GitHub Copilot. Their proof of value has really proven to be beneficial in a lot of their development aspects. Some of them have tougher security controls in their corporate environments. One of them is SSL inspection through their firewall/NVA. This had lead to the dreadful error:
[CopilotClientManager Information] statusNotification: Warning: The pending stream has been canceled (caused by: self-signed certificate in certificate chain)
[CopilotClientManager Error] [ghostText] Error on ghost text request: FetchError: The pending stream has been canceled (caused by: self-signed certificate in certificate chain)
The GitHub engineering team is aware of the problem. While the tools continue to improve and a more native fix / solution can hopefully be baked in, as I tell my customers, always open a support ticket to help the engineering team navigate these issues. If your organization is doing SSL inspection and you have access to the Root certificate (and it is also installed and trusted in the Windows Certificate Store), here is what I suggest to do to help resolve this error for both Visual Studio and Visual Studio Code.
It helps to also view and collect the diagnostics for GitHub Copilot. To do this, you can look at the documentation for Visual Studio and Visual Studio Code.
The GitHub team provides possible ways in the documentation to help Visual Studio and Visual Studio Code mitigate / resolve the errors:
- Configure a different proxy that does not intercept secure connections.
- If you are using a corporate proxy, contact your IT department to see if they can configure the proxy to not intercept secure connections.
Visual Studio Code
If your Root certificate has been installed and trusted in your Windows Certificate Store machine, but GitHub Copilot isn’t detecting them, it may help you to know the mechanisms that GitHub Copilot uses to find certificates.
- On Windows, Copilot uses the win-ca package.
- On macOS, Copilot uses the mac-ca package.
- On Linux, Copilot checks the standard OpenSSL files
/etc/ssl/certs/ca-certificates.crt and /etc/ssl/certs/ca-bundle.crt
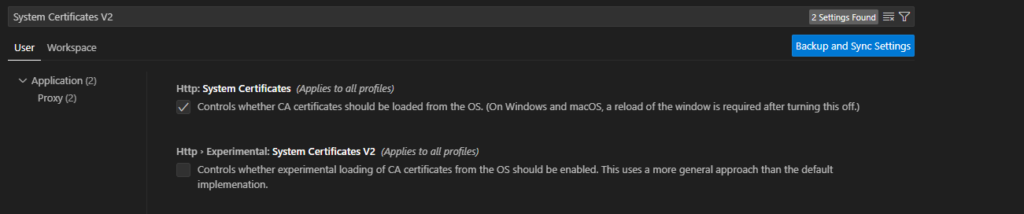
You can also use the experimental V2 feature in Visual Studio Code to allow loading of CA certificates from the OS. To do so, open the settings (ctrl+`) and navigate to the Application -> Proxy settings. Check the System Certificates V2 option. There is also a System Certificates option. You can leave this enabled, but the V2 option must be enabled. This is a different implementation, and the older option does not work. Once enabled, please relaunch Visual Studio Code.
Visual Studio
In Visual Studio, the above options do not work. As GitHub Copilot is based off of node, you have the options to enable GitHub Copilot to use custom certificates.
This requires providing a certificate (in pem format) containing all the trusted root CA in the enterprise, and setting and env var to pass this cert to node wen it initializes. This is done in 2 steps:
- First save the certificate somewhere accessible on your machine.
- Run the following command to globally set the NODE_EXTRA_CA_CERTS environment variable.
setx NODE_EXTRA_CA_CERTS "C:\path\to\multi.pem"
If Visual Studio is open, please make sure to relaunch it.
Other solution
If you are still experiencing the problem, the GitHub team as proposed a fix that can help as per the GitHub issue here. They recommend to do the following:
Add this or both options to your user settings: (F1 > Preferences: Open User Settings (JSON))
|
1 2 3 4 5 6 7 |
"github.copilot.advanced": { "debug.useNodeFetcher": true } "github.copilot.advanced": { "debug.useElectronFetcher": true } |
Hope this helps and happy GitHub Copiloting!
